AWS VPC
VPC lets you provision a logically isolated section of the Amazon Web Services (AWS) cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address ranges, creation of subnets, and configuration of route tables and network gateways.
Amazon VPC comprises a variety of objects that will be familiar to customers with existing networks:
Subnet: A segment of a VPC’s IP address range where you can place groups of isolated resources.
Internet Gateway: The Amazon VPC side of a connection to the public Internet.
NAT Gateway: A highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet.
Let’s design our VPC diagram as follow:VPC Design Architecture
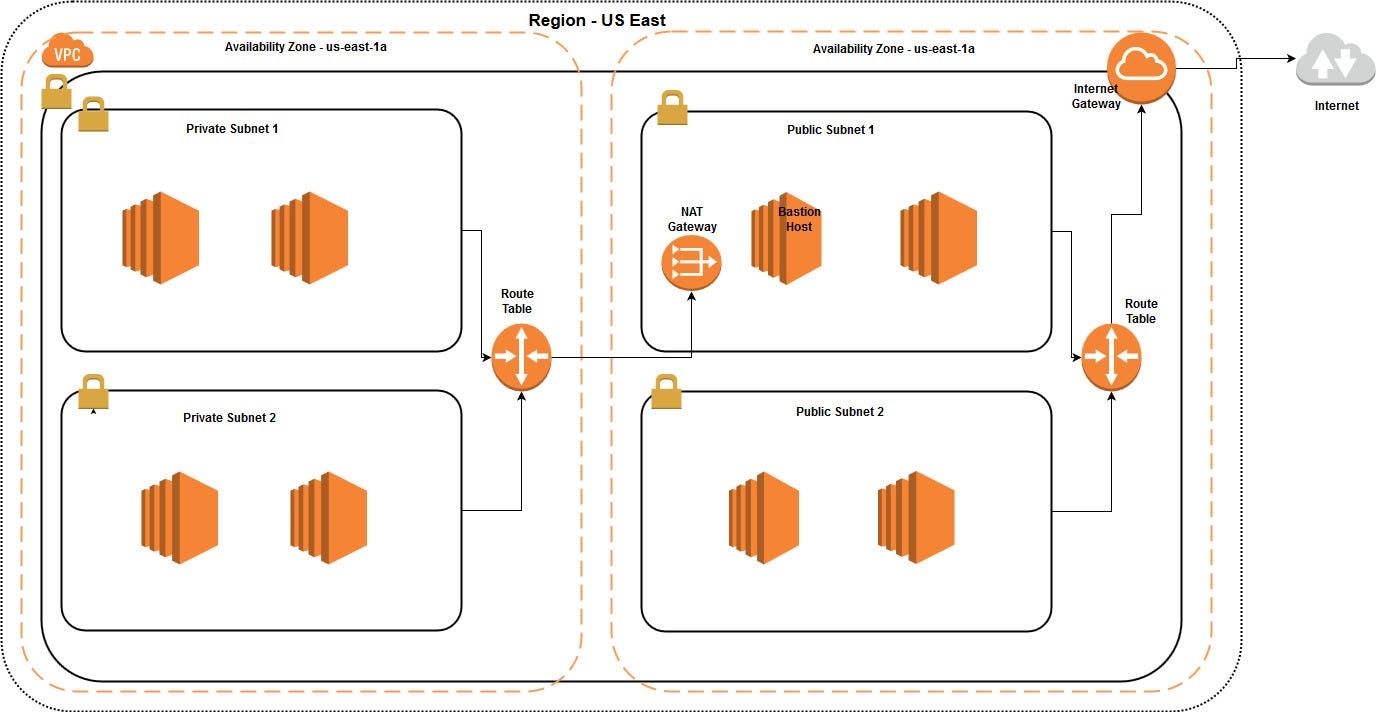
We have to decide the design for the VPC base on the requirement.Here we are going to create VPC with two private subnets and two public subnets as mentioned in the above diagram. Let’s do the implementation step by step.
Step 01 : Design the VPC architecture
Decide the IP range for the VPC before creating the VPC. Here we are using 10.1.0.0/24 as the CIDR block.This CIDR block assigns 256 IP address for the VPC. Hence we are using 4 subnets for the VPC we have to divide the 256 IP addresses among 4 subnets. I’ll explain how to calculate number of IP addresses for the VPC and divide them between subnets.
CIDR block for the VPC -> 10.1.0.0/24
Number of IP address -> 2^(32–24) -> 2⁸ -> 256
Assuming equal number of IP addresses for the each subnet,
Number of IP addresses for a subnet = 256/4 = 64
Here is the IP address distribution for the above 4 subnets
Public Subnet 1 -> 10.1.0.0/26 (IP range — 10.1.0.0–10.1.0.63)
Public Subnet 2 -> 10.1.0.64/26 (IP range — 10.1.0.64–10.1.0.127)
Private Subnet 1-> 10.1.0.128/26 (IP range — 10.1.0.128–10.1.0.191)
Private Subnet 2 ->10.1.0.192/26 (IP range — 10.1.0.192–10.1.0.255)
We are going to implement VPC according to the above details
Step 02 : Log in to AWS management console
Log in to the AWS management console and go to the VPC under Services.
Step 03 : Create VPC
Go to “Your VPCs” in the side bar and Click on the “Create VPC “. This will pop up a window for the VPC creation. Add a name and CIDR block (10.1.0.0 /24 according to our example) for the VPC. Keep other fields with default values. Finally create the VPC.
Note : VPC belongs to only one region.Create VPC

Step 4 : Create Subnets inside VPC
Go to the Subnets from the side bar once VPC creation getting completed. Click on the “Create Subnet” button and pop up will come for subnet creation. Let’s create public subnet 1 as mentioned below. Select the previously created VPC and select availability zone from the list.Create Subnet

Note : Create other 3 subnets also as mention above diagram. Insert the IPv4 CIDR block according to the IP ranges decided in the step 1. Keep public-subnet-1 and private-subnet-1 inside the same availability zone and public-subnet-2 and private-subnet-2 inside the another availability zone to increase the availability. You can see all the subnets as follows once completed the process. 5 IP addresses out of all the IP addresses of the subnet are reserved for the internal usage.This is the reason to display number of Available IPv4 as 59 .

Step 05 : Create Route Tables and Associate with subnets
Next we have to create route tables for subnets. Route table contains a set of rules, called routes, that are used to determine where network traffic is directed. We can associate all the public subnets into one route table and private subnets into another route table. Go to the Route Tables from side bar and Click the “Create Route Table”. You can create route table giving a name and selecting your VPC. It will display as follows once created the two route tables.Create Route Tables

You can see non of the subnets are explicitly associated with route table. We have to associated them manually. As mentioned before, we are going to assign two public subnets into public route table and two private subnets into private route table. Select the “sample-public-RT” subnet from the list and go to the “Subnet Associations” tab under you route table list.Click “Edit” and select two public subnets from the list.Do the same for associate private subnets to the private route table.

Note: One route table can be associated with multiple subnets. But one subnet can be associated with only one route table.
Step 6 : Create Internet Gateway and associated with public route table
Now we have to create Internet Gateway and associate public route table with the created Internet Gateway. Internet Gateway allows communication between instances in your VPC and the public internet. all the instances attached with the subnets can be connected to the internet once we associated their route table with the Internet Gateway. Therefore we need to create Internet gateway and attach public route table with it. Normally we are not associate private route tables with the Internet Gateway hence they are not directly connect to the public internet.
Go to the Internet Gateway from the side bar and create new Internet Gateway giving a name for it. Once the Internet Gateway created, It is not attached with any VPC. So we need to attach created VPC with our VPC. Therefore select the Internet Gateway from the list and go to the “Action” drop down. Then select “Attached to VPC” and select our VPC from the list.
Now we have public route table which associated with the Internet Gateway.
Step 07 : Create NAT Gateway and Associate with private route table.
Now we are one step behind to complete our VPC design. Based on the best practice and best security concerns we are deploy our applications and DB servers inside private subnets. Then outsiders cannot access the applications and DB servers. But sometimes Private subnets might needed to connect public internet due to get some updates for the application(Eg: Install Java inside private instance). Therefore we are using NAT gateways to connect private subnets into the internet. NAT Gateways are located inside public subnet. Once private route table receives traffic from the private subnet, It will be directed to the NAT gateway based on route table records and then NAT Gateway communicate with the public internet.
Go to the NAT Gateway option from the side bar and click “Create NAT Gateway”. Then it will popup the NAT Gateway creation window. Select your private subnet from the list. Create New Elastic IP and allocate it to the NAT Gateway.

Note : Elastic IP address works as public address and it will visible to out side.
We are done with our VPC design. We have to create private instance inside private subnet and public instance inside public subnet. You will receive .pem file when creating the EC2 instance. Keep it in the safe location. It will need to log into the instance later.
Note : We are not going to explain the EC2 creation steps here. Please refer this link to get guidance for EC2 creation.
Additional Scope : Access the EC2 instances
You can log in to public instances located in public subnet with following ways.
Linux users
ssh -i “<private key .pem name>” ec2-user@<public ip of instance>.
Windows Users
Install putty in your local machine and create the connection through the putty interface.
But you cannot log into the private instances using above method. So I’ll explain how to log in to the private instances using putty. This will help to windows users.
Download putty from here and install it following the wizard. You will get several application with the putty installation like putty, puttygen, pageant, etc..
Normally putty does not support for the .pem file. So we have to convert our .pem file into .ppk format as the first step.
2. Open the puttygen and click Load button. Select your .pem file of the public instance and click Save private key button. Now you have a .ppk file for your EC2 instance.
3. Open the Pageant and add your .ppk file clicking on the Add Key button.
4. Now we are going to create bastion instance.Bastion instance locates inside the public subnet and we are going to connect private instance through the bastion instance. In this example we are going to use public instance we are created before as the bastion instance.
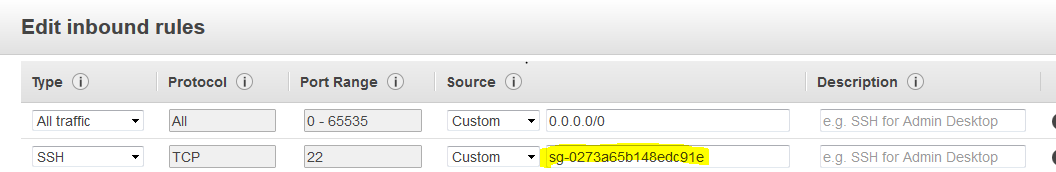
Go to the Security group of the Private instance and add inbound rule to allow traffic from bastion instance as follow. Add the bastion instance to the Source as highlighted in below image.
If you need to know more about bastion instance, read this article.
5. Open Putty and add your public instance public IP address into the Host name. Then select Data navigation tab from the side bar and add “ec2-user” as the auto login user(This is depend on the OS type of the EC2). Now go to the SSH from side bar and Select Auth. Tick the Allow agent forwarding. Click Open to login into your bastion instance. Please refer below image.

6. Now you are logged into the Bastion instance and you can log into your private instance simply typing following command.
ssh ec2-user@<IP of private instance>.
Logging part is mentioned as additional scope and hope it will help you in the future.
Last updated